Even novices can easily fully grasp its functions. copyright stands out with a big choice of buying and selling pairs, affordable expenses, and higher-stability specifications. The support staff can also be responsive and generally Prepared to aid.
Plan options must set extra emphasis on educating industry actors close to key threats in copyright as well as role of cybersecurity although also incentivizing increased protection benchmarks.
Significant: Before starting your verification, please make sure you reside within a supported state/location. You'll be able to check which states/locations are supported listed here.
Be aware: In unusual situation, depending on cellular copyright options, you might require to exit the web site and try once more in a number of several hours.
Notice: In unusual conditions, dependant upon cellular copyright settings, you may need to exit the webpage and check out once more in a couple of hours.
Enter Code even though signup to receive $a hundred. I absolutely adore the copyright providers. The one challenge I have experienced While using the copyright though is the fact that From time to time Once i'm buying and selling any pair it goes so sluggish it requires without end to complete the extent then my boosters I take advantage of for that degrees just operate out of your time as it took so prolonged.
In advance of sending or obtaining copyright for the first time, we endorse examining our suggested best techniques In relation to copyright security.
Facts sharing companies like copyright ISAC and SEAL-ISAC, with associates throughout the copyright field, perform to Increase the pace and integration of endeavours to stem copyright thefts. The market-large response into the copyright heist is a good illustration of the value of collaboration. Still, the 바이비트 need for at any time faster action continues to be.
Several argue that regulation successful for securing banking institutions is much less effective in the copyright House mainly because of the marketplace?�s decentralized character. copyright wants much more security polices, but In addition it desires new remedies that keep in mind its variations from fiat financial establishments.
These risk actors ended up then able to steal AWS session tokens, the short term keys that assist you to request short term qualifications to your employer?�s AWS account. By hijacking active tokens, the attackers have been ready to bypass MFA controls and acquire use of Safe and sound Wallet ?�s AWS account. By timing their efforts to coincide With all the developer?�s usual do the job hours, Additionally they remained undetected right up until the particular heist.
The copyright Application goes over and above your standard trading application, enabling buyers To find out more about blockchain, receive passive cash flow by means of staking, and invest their copyright.}
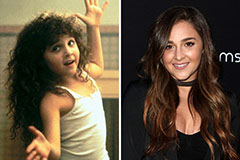 Alisan Porter Then & Now!
Alisan Porter Then & Now! Heath Ledger Then & Now!
Heath Ledger Then & Now! Seth Green Then & Now!
Seth Green Then & Now! Robbie Rist Then & Now!
Robbie Rist Then & Now! Megyn Kelly Then & Now!
Megyn Kelly Then & Now!